In the digital age, trust is everything. Whether you are signing into your online banking portal, sending an encrypted email, or deploying thousands of IoT devices across the globe, you rely on one invisible yet critical component—Public Key Infrastructure (PKI).
PKI is the foundation of secure digital communication. It is a combination of hardware, software, policies, and standards that work together to create, distribute, manage, and revoke digital certificates. These certificates verify that an entity—whether a person, device, or application—is exactly who or what it claims to be.
At its core, PKI provides:
-
Authentication – Proving identity.
-
Confidentiality – Ensuring only the intended recipient can read data.
-
Integrity – Verifying that data has not been altered.
-
Non-repudiation – Ensuring that actions cannot be denied later.
From securing websites with HTTPS to enabling secure email communication, PKI underpins the very fabric of digital trust. But while PKI may sound straightforward, in practice, it is a complex ecosystem that demands meticulous planning, governance, and continuous monitoring.
Why PKI Projects Are Consulting-Level Complex
Deploying PKI isn’t like installing an antivirus program. It’s not just an IT project—it’s a strategic initiative that touches security, compliance, legal frameworks, and even business continuity planning. Organizations often underestimate this complexity, which can lead to misconfigurations, outages, or compliance failures.
The Policy and Governance Dimension
PKI isn’t only about issuing certificates—it’s about defining who can issue them, under what circumstances, and with what level of assurance. Certificate Policies (CP) and Certification Practice Statements (CPS) are governance documents that set the rules of trust. Without these policies, a PKI may fail audits or introduce security loopholes.
The Integration Challenge
PKI integrates with numerous systems—Active Directory, email platforms, VPNs, mobile device managers, and cloud services. Each integration comes with its own challenges, from protocol compatibility to automation of certificate enrollment.
Lifecycle Management and Compliance
PKI isn’t static. Certificates expire. Algorithms become obsolete. Regulatory requirements evolve. A neglected PKI can quickly become a liability, leading to expired certificates that cause outages or vulnerabilities that hackers can exploit.
Consulting-grade PKI design ensures:
-
Strong architecture
-
Defined governance
-
Scalable automation
-
Disaster recovery readiness
-
Audit compliance
PKI Architecture: The Building Blocks of Digital Trust
A well-designed PKI has multiple components, each with a distinct role in the trust chain.
Root Certificate Authority (Root CA)
The Root CA is the ultimate source of trust. It’s typically kept offline for security, because if the root is compromised, the entire PKI collapses. Think of it as the “master key” of your digital trust ecosystem.
Intermediate and Issuing CAs
These act under the root’s authority and handle day-to-day certificate issuance. Multiple issuing CAs can be deployed for redundancy and segregation of duties.
Registration Authority (RA)
The RA validates the identity of certificate requestors before certificates are issued. It ensures that only legitimate entities receive credentials.
Hardware Security Modules (HSMs)
HSMs secure private keys in tamper-proof hardware. For compliance with standards like FIPS 140-2, HSMs are non-negotiable in high-security environments.
Certificate Repositories and Directories
Repositories store and distribute certificates and revocation lists (CRLs). They enable clients to verify certificate validity.
Revocation Infrastructure
Whether through Certificate Revocation Lists (CRLs) or Online Certificate Status Protocol (OCSP), revocation ensures that compromised or expired certificates are invalidated promptly.
The PKI Lifecycle: A Consulting Approach
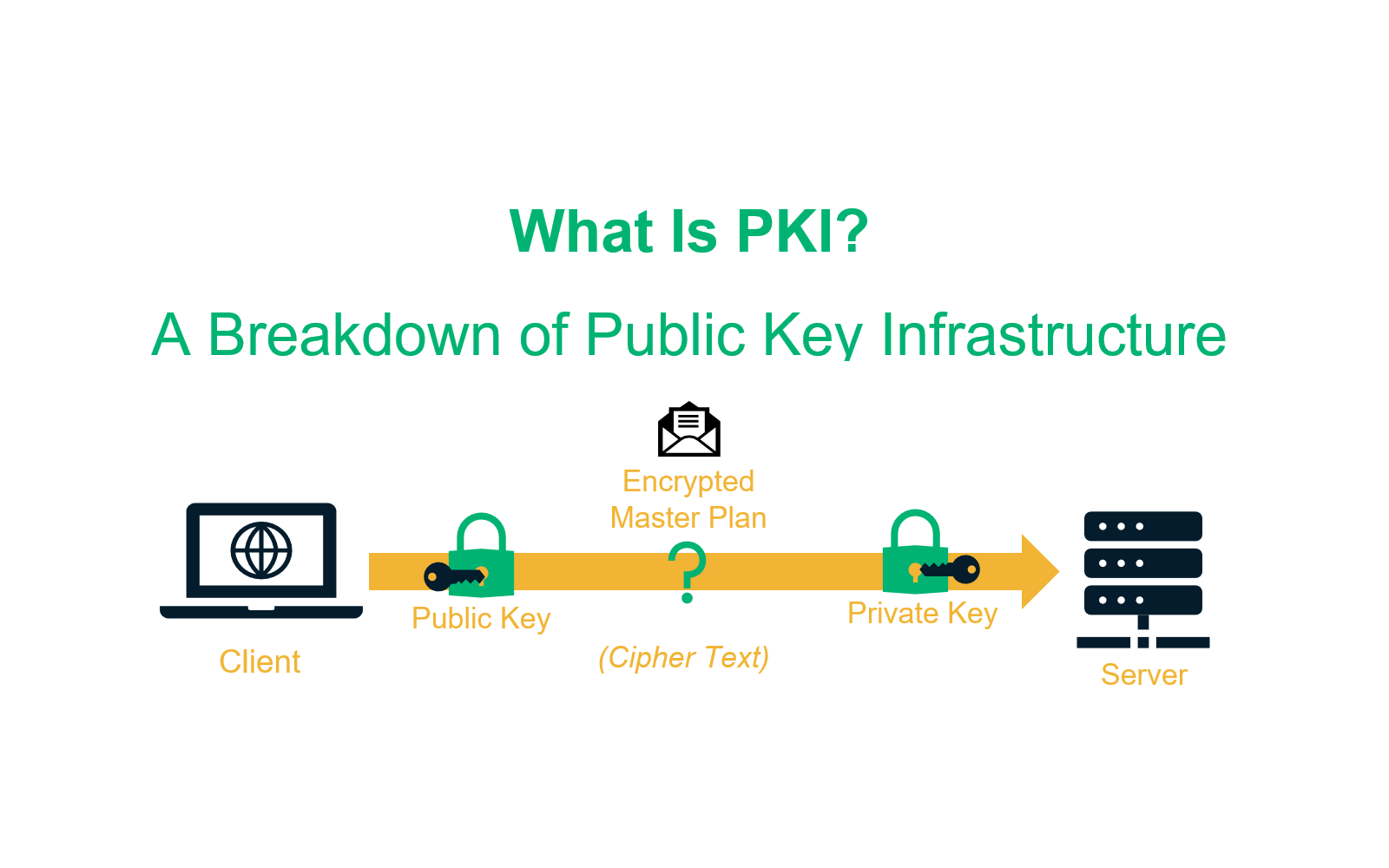
A consulting-grade PKI implementation follows a structured methodology. Let’s break it down into seven phases:
Discovery and Assessment
This phase involves understanding:
-
Current security posture
-
Existing certificate usage
-
Integration points
-
Regulatory requirements
-
Scalability needs
-
Cloud or hybrid environments
Key activities include stakeholder interviews, system inventories, and compliance gap analysis.
Policy and Governance Design
Here, consultants draft:
-
Certificate Policy (CP): The “what” of PKI—objectives, usage constraints, and assurance levels.
-
Certification Practice Statement (CPS): The “how”—detailed operational procedures for issuing and managing certificates.
Clear policies ensure compliance and avoid trust erosion.
Architecture Design
A robust PKI architecture balances:
-
Security (HSM integration, multi-tier CA hierarchy)
-
Scalability (to handle future growth and IoT)
-
Resilience (high availability and disaster recovery)
-
Compliance (alignment with regulations and audits)
Design decisions include:
-
Number of CAs
-
Offline/online segregation
-
Network segmentation
-
Automation strategies
Deployment
This is where theory meets reality. Deployment includes:
-
Building the root CA in an offline environment
-
Conducting key ceremonies
-
Setting up issuing CAs
-
Integrating with HSMs
-
Configuring CRL and OCSP responders
-
Automating enrollment (e.g., with SCEP or ACME)
Documentation is critical—every step must be recorded for auditability.
Validation and Testing
Testing ensures:
-
Certificates issue correctly
-
Revocation works (CRL and OCSP)
-
Failover systems function under stress
-
Security controls withstand penetration testing
Transition and Handover
After deployment, consultants hand over:
-
Architecture documentation
-
Operational runbooks
-
Incident response plans
-
Training for internal teams
Ongoing Operations
PKI requires continuous monitoring:
-
Certificate expirations
-
Compliance with evolving standards
-
Performance of OCSP responders
-
CRL size and distribution health
-
Key rollover planning
Managed PKI or co-managed services are popular to keep PKI healthy and aligned with best practices.
Common PKI Pitfalls and How to Avoid Them
Even large enterprises fall into traps. Here are the most frequent missteps:
Neglecting Governance
Skipping policy documents like CP and CPS can cause audit failures or create ambiguities that attackers exploit.
Poor Key Management
Storing CA private keys on standard servers instead of HSMs is a recipe for disaster. A compromised key compromises your entire trust ecosystem.
Inadequate Revocation Handling
If CRLs are too large or OCSP responders are unreliable, clients may fail to validate certificates, leading to service outages.
Ignoring Automation
Manual certificate issuance and renewal lead to human error and downtime. Automation tools are essential, especially at enterprise scale.
Lack of Monitoring
Expired certificates can cause major outages—remember the global service disruptions caused by overlooked certificate expirations? Continuous monitoring prevents this.
Advanced PKI Considerations for Modern Enterprises
PKI is evolving. Here are some key trends and challenges shaping the future:
Cloud and Hybrid Deployments
Organizations are increasingly adopting cloud-based PKI as a Service for scalability and reduced operational overhead. Hybrid models—where roots remain on-prem while issuing CAs operate in the cloud—are also popular.
PKI for IoT
Billions of IoT devices need identity and encryption. PKI provides a scalable solution for authenticating devices, securing firmware updates, and enabling encrypted communications.
Post-Quantum Cryptography (PQC) Readiness
Quantum computing threatens current cryptographic algorithms like RSA and ECC. Organizations must begin planning PKI architectures that can adopt PQC algorithms without a complete redesign.
Decentralized PKI
Blockchain and decentralized identity frameworks are emerging alternatives to traditional hierarchical PKI. While promising, these are still in early stages and require careful evaluation before adoption.
Real-World Use Cases
Financial Services
Banks use PKI for:
-
Securing customer transactions
-
Enabling strong authentication for employees
-
Digital signing of high-value transactions
-
Securing SWIFT communications
Healthcare
PKI ensures:
-
Secure exchange of patient records
-
Compliance with HIPAA and other regulations
-
Integrity of medical device communications
Energy and Utilities
PKI enables:
-
Secure communication between SCADA systems
-
Authentication of field devices
-
Preventing unauthorized access to critical infrastructure
Government
National ID systems, e-passports, and secure communications for government agencies rely heavily on PKI.
Cost Considerations: PKI Is an Investment in Trust
PKI costs vary dramatically:
-
Minimal implementations (e.g., Let’s Encrypt for a few web servers) cost almost nothing.
-
Enterprise-grade PKI with HSMs, redundancy, and compliance features can cost hundreds of thousands annually.
Costs include:
-
Hardware (HSMs, servers)
-
Software licenses
-
Consulting and deployment
-
Ongoing operations and monitoring
However, the cost of not having a secure PKI—data breaches, service outages, compliance fines—can be far greater.
Building a Future-Proof PKI Strategy
To make PKI a strategic asset:
-
Align with business goals: Understand what systems need PKI and why.
-
Plan for automation: Use enrollment protocols and certificate management platforms.
-
Embed compliance: Design CP/CPS for current and future regulations.
-
Enable flexibility: Prepare for PQC, cloud integration, and hybrid models.
-
Monitor continuously: Use real-time visibility tools to detect anomalies and prevent outages.
Final Thoughts: PKI as a Business Enabler
PKI is more than an IT necessity—it’s a business enabler. It enables secure customer interactions, regulatory compliance, and resilience against cyber threats. But achieving a robust PKI requires consulting-grade expertise: deep technical knowledge, rigorous governance, and a strategic mindset.
In short, PKI is the silent guardian of digital trust. Organizations that invest in doing PKI right—not just deploying it, but governing and maintaining it—will stand at the forefront of secure digital transformation.
